👋 Hello and Welcome,
In this blog, you will learn the Secure way to control access to AWS resources. Don’t use the AWS root account credentials to access AWS services; don’t share the credentials with anyone else. Start by creating an IAM User with a role that has access to all resources as the Root except the account’s security credentials.
how to configure the AWS Command Line Interface (AWS CLI) settings to interact with AWS services. After installing AWS CLI, you will have to configure it to use it, before that we will learn what is IAM? and why it is so important.
🔶 What is IAM (Identity and Access Management)?
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. With IAM, you can centrally manage permissions that control which AWS resources users can access. You use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources.
When you create an AWS account, you begin with one sign-in identity that has complete access to all AWS services and resources in the account. This identity is called the AWS account root user and is accessed by signing in with the email address and password that you used to create the account. We strongly recommend not using the root user for your everyday tasks.
Simply, Authentication means Who can access the resources. when we log in as root users, we can access AWS resources. suppose in a large organization so many developers or cloud engineers are working on particular infrastructure projects it's not a secure way to give all access to every person. So you can allow users to access resources with permissions which are called Authorization.
🔶 What is the IAM Role?
An IAM role is an IAM identity that you can create in your account that has specific permissions. An IAM role is similar to an IAM user, in that it is an AWS identity with permission policies that determine what the identity can and cannot do in AWS. However, instead of being uniquely associated with one person, a role is intended to be assumed by anyone who needs it.
🔶 What are IAM policies?
IAM policies define permissions for an action regardless of the method that you use to perform the operation. For example, if a policy allows the GetUser action, then a user with that policy can get user information from the AWS Management Console, the AWS CLI, or the AWS API.
🔶 Configure the AWS CLI
First, let’s see how to check whether AWS CLI has been successfully installed in your system. For that, just type in the following command in your command prompt:
aws --version
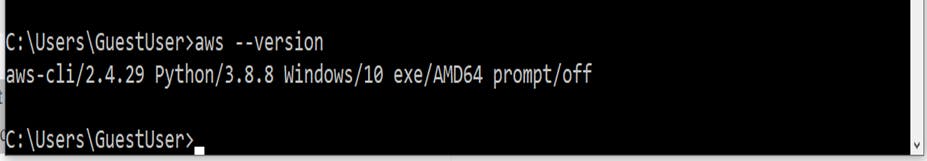
Once you are sure that AWS CLI is successfully installed, you need to configure it to start accessing your AWS Services through AWS CLI.
If you are first setting up the CLI, there are some additional steps to interact with AWS. You need to create a user profile using the command “aws configure” but get your AWS access and the secret access keys before starting it. If you do not have them, then you have to create an IAM user, In AWS, interacting with services requires explicit permissions defined by your IAM user following these steps:
Step 1: Log in to AWS Management Console as a root user.
Step 2: Create an IAM user
Log into your AWS dashboard and search for IAM (Identity Access Management) from the Find services search bar available in your dashboard or services a security identity and compliance->IAM (Identity and Access Management).
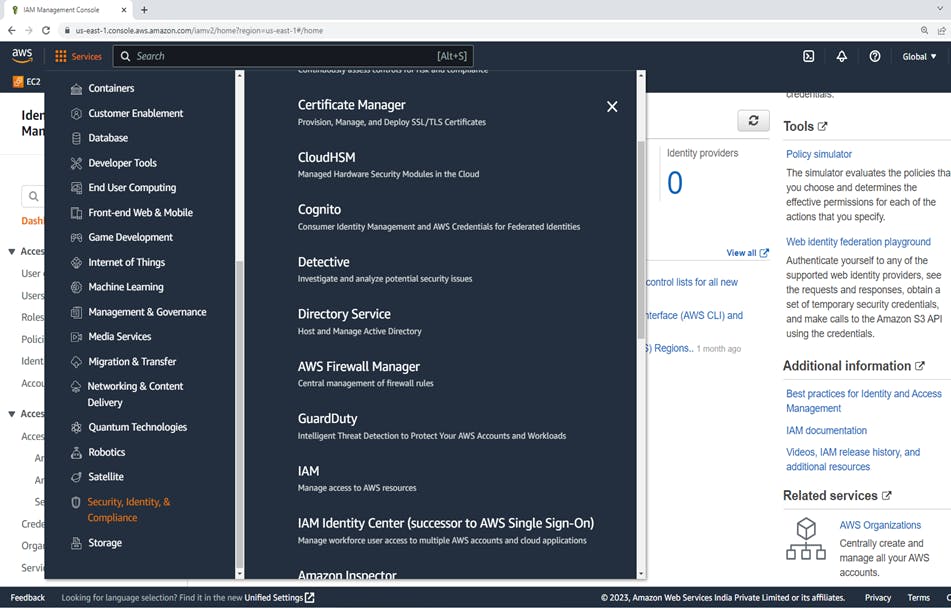
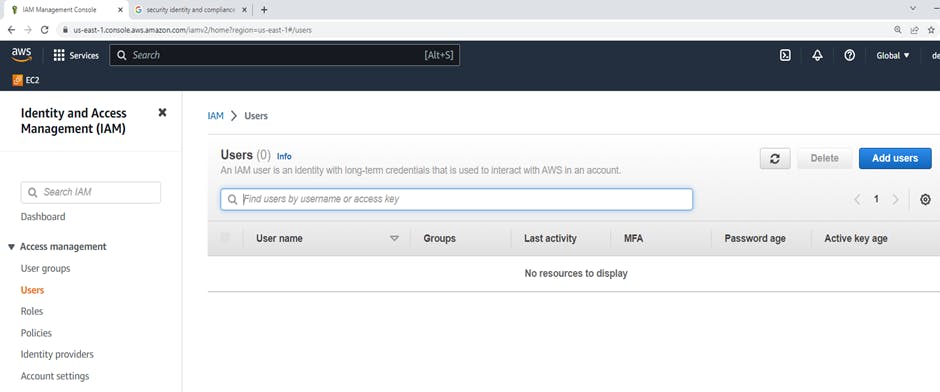
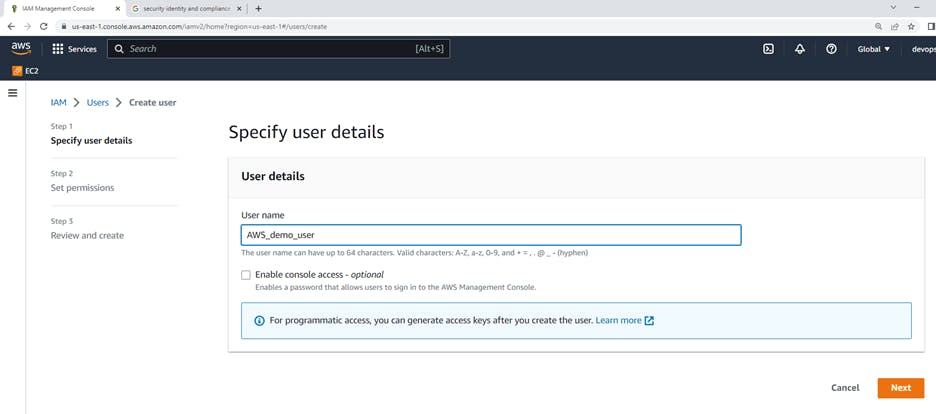
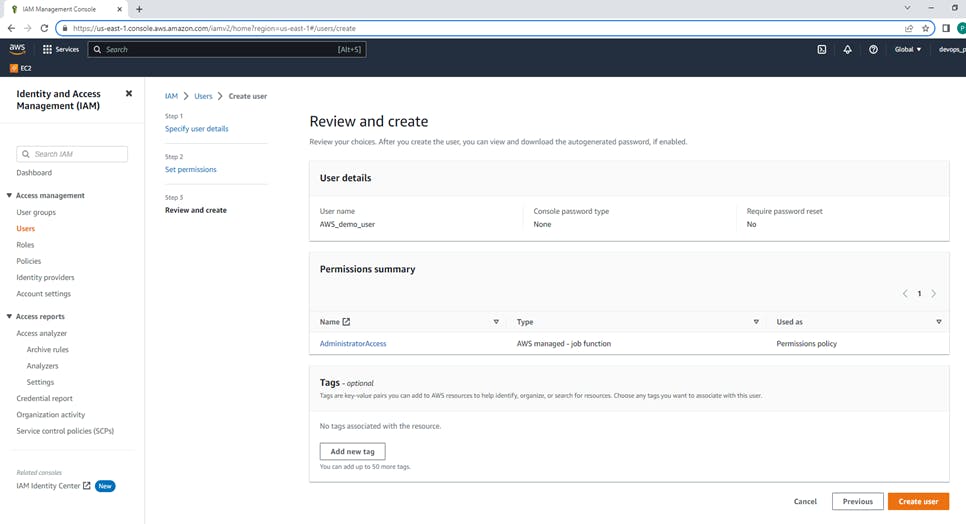
Click on IAM --> Users--> click on Add users. After that Click on Add users, Create user window will appear. Create user "AWS_demo_user"
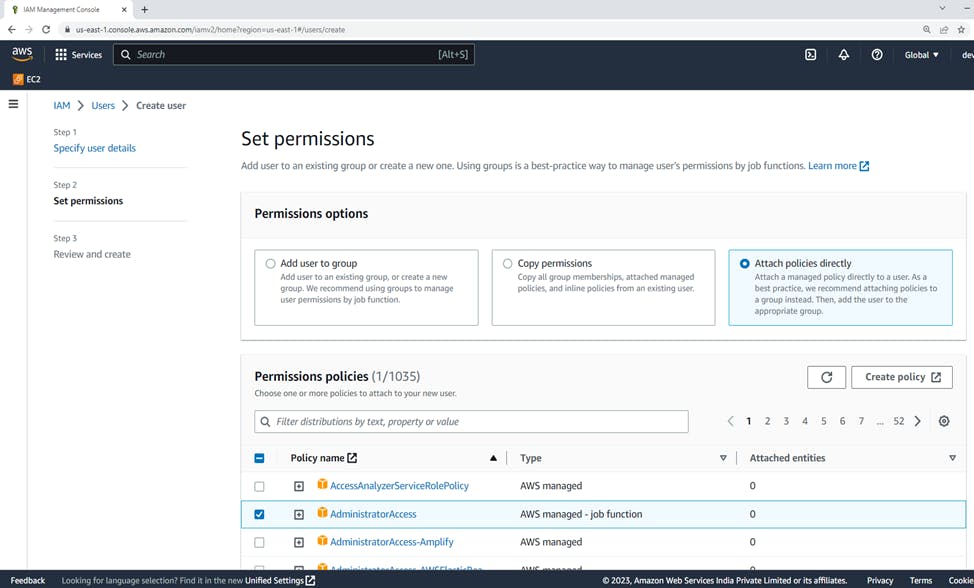
select the option Attach policies directly, you can give "AdministratorAccess"
Click Next, complete step 3 in user creation ---> Review and "Create user" So Have successfully created "AWS_demo_user"
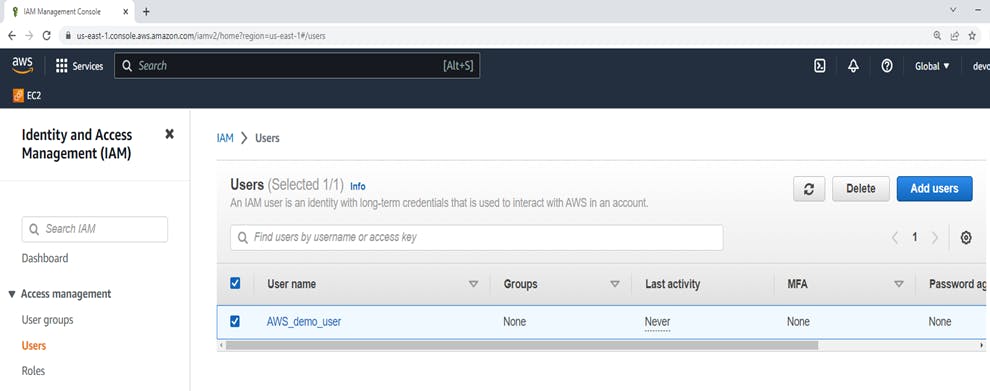
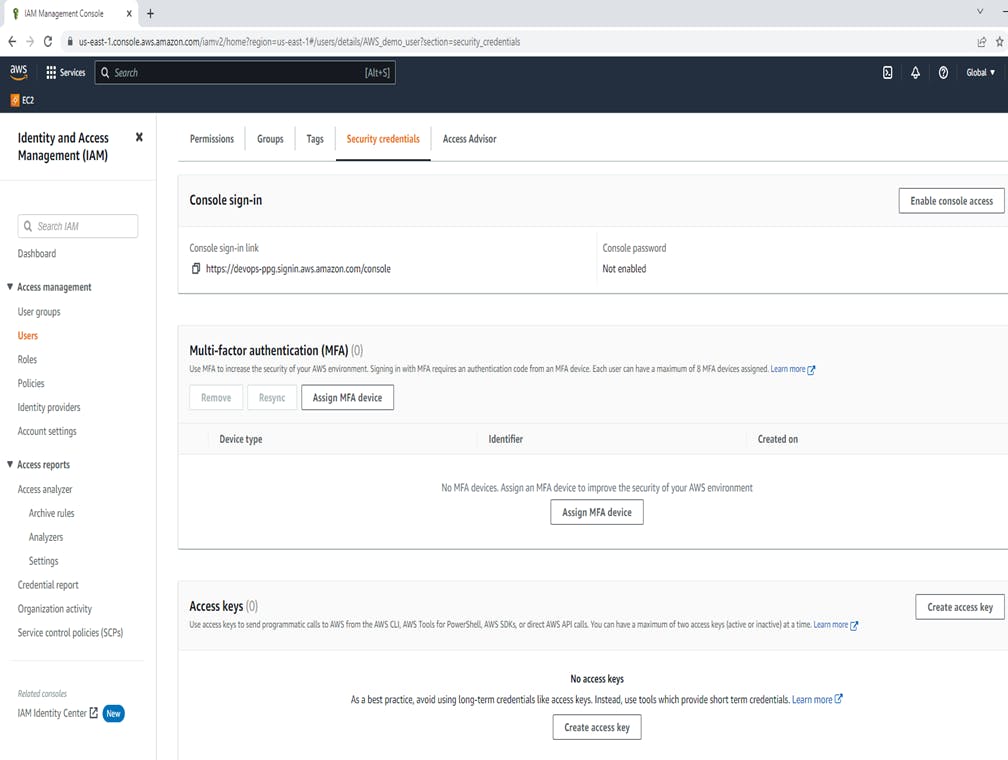
Click on "AWS_demo_user" and it's selected... After clicking go to Security Credentials

In Security Credentials Tab Scroll down there are the following available options.
1. Console sign-in,
2. Multi-factor Authentication(MFA),
3. Access Keys
4. SSH public keys for AWS CodeCommit
5. HTTPS Git credentials for AWS CodeCommit,
6. Credentials for Amazon Keyspaces (for Apache Cassandra),
7. Signing certificates (X.509) these are options available.
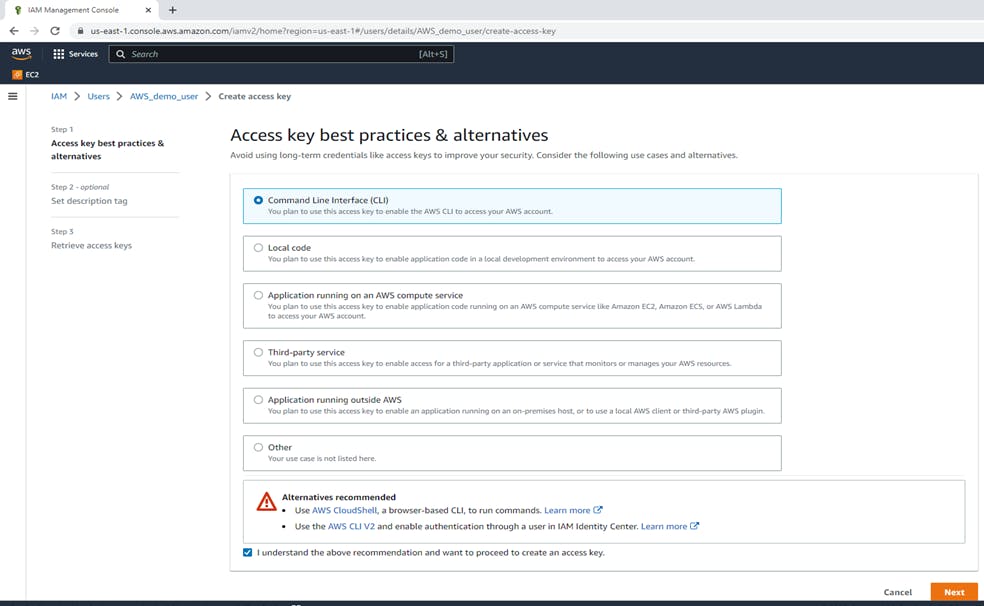
So here, we use Access keys to send programmatic calls to AWS from the AWS CLI. Select the option Command Line Interface(CLI) --> select the checkbox for recommendations -->click on Next.
Set description tag "key_for_aws_demo_user"
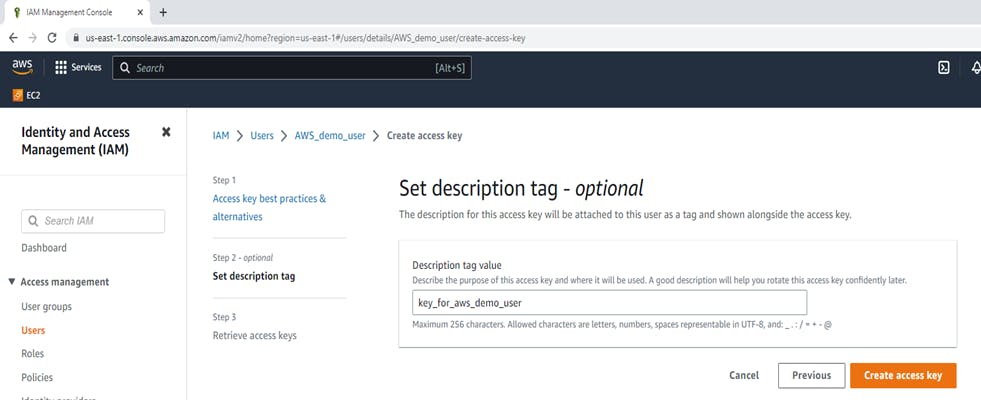

we have created successfully Access Key, Download that .csv file. we need this Access Key and the Secret access key for "aws configure".
Never store your access key in plain text, in a code repository.
Do not generate the access keys, if not required.
Enable least-privilege permissions.
Rotate access keys regularly.
Step 3: AWS CLI Task
For general use, the aws configure command is the fastest way to set up your AWS CLI installation. When you enter this command, the AWS CLI prompts you for four pieces of information:
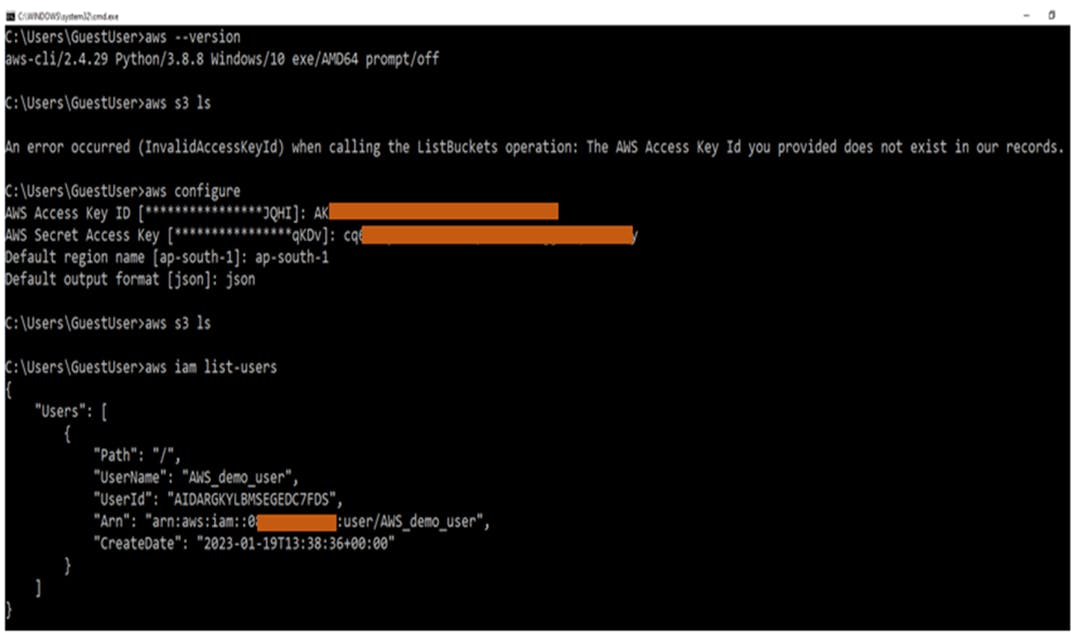
Open a command prompt by pressing the Windows Key + r to open the run box and enter cmd and press the OK button, and at the command prompt use the command. aws --version for checking aws version. So now, let's check whether you can access AWS services or not with the simple command aws s3 ls if it gives the error Access key does not exist in our records, so you need to configure it.
After the "aws configure" command enter Access Key ID and the Secret access key from the downloaded .CSV file. successfully if we run the command aws s3 ls it won't give any error message. and we can check the list of all users with the help of aws s3 ls
aws s3 ls
aws configure
After "aws configure" successfully if we run the command aws s3 ls it won't give any error message. You can also check the list of all IAM users with AWS CLI using the following command.
aws iam list-users
🥳🥳 Congratulations!
You have learned how to create an IAM user through the AWS management console. How to attach policies directly to the user and with the help of an access key & secret access key how to configure an AWS Account through AWS CLI. Also learned how to check a list of IAM users with the AWS CLI command.
So it can be beneficial to do some research and find the opportunities that can be most helpful in building your career & becoming a part of the cloud computing world.
If you enjoyed this article, share it with your friends and colleagues!
